Defend your device from
Our behavioural models perform deep scans to spot fake and repackaged apps, even when disguised with similar branding
The new attack vector
Clone and fake apps are increasingly weaponized by cybercriminals, exploiting the rapid proliferation of app ecosystems to deceive users and compromise data. These counterfeit apps often mimic trusted brands, targeting users through unofficial app stores, SMS, and WhatsApp.
Clone apps mimicking banking apps trick users into entering their credentials, leading to direct financial theft and account takeover
Modded clones of gaming apps lure users with premium unlocks but quietly install adware and spyware
Counterfeit health apps harvest sensitive medical data by impersonating legitimate healthcare brands
Fake public service apps like digital challan portals steal personal data while pretending to offer official services by exploiting urgency to trap victims
targeted by attackers in last year
recorded in last 12 months
with growing evasion techniques
Built For Trust. Designed For Mobile Security.
Our deep learning model continuously learn from real-world data to detect spyware, repackaged apps and evasive threats for proactive mitigation
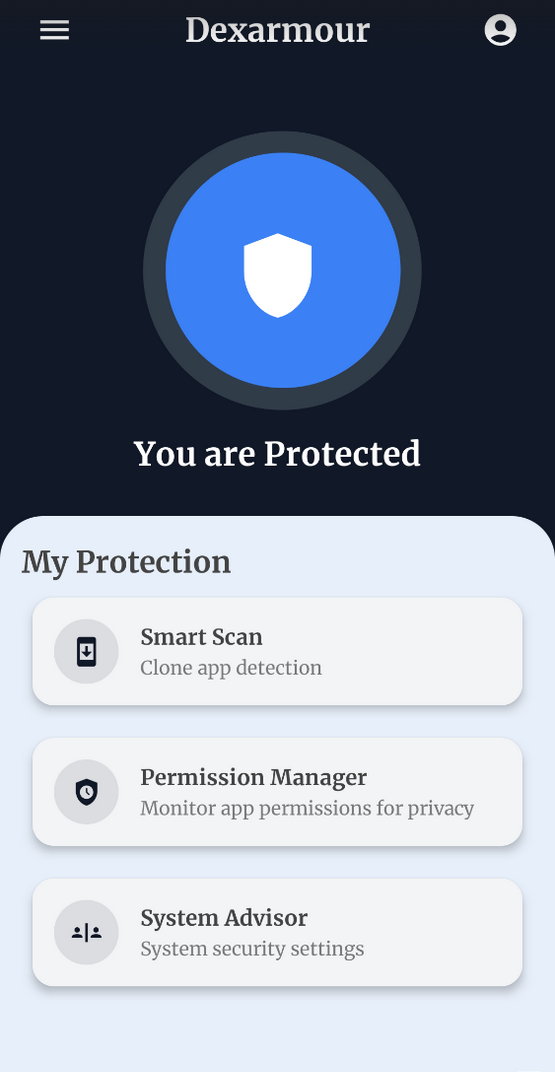
Stay safe from clones, trackers and fake apps
Supported by


MVP Winner in Fake & Clone App Mitigation Category in Cyber Security Grand challenge 2.0
Latest Insights
Practical guidance and research from the Dexarmour team.
